Date: 06/01/1985A set of network protocol layers that work together. The OSI Reference Model that defines seven protocol layers is often called a stack, as is the set of TCP/IP protocols that define communication over the internet. The term stack also refers to the actual software that processes the protocols. So, for example, programmers sometimes talk about loading a stack, which means to load the software required to use a specific set of protocols. Another common phrase is binding a stack, which refers to linking a set of network protocols to a network interface card (NIC). Every NIC must have at least one stack bound to it.
Internet protocol stack provides a connection oriented reliable branch (TCP) and an connectionless unreliable branch (UDP) both build on top of the Internet Protocol. The Internet Protocol layer in the TCP/IP protocol stack is the first layer that introduces the virtual network abstraction that is the basic principle of the Internet model. All physical implementation details (ideally even though this is not quite true) are hidden below the IP layer. The IP layer provides an unreliable, connectionless delivery system. The reason why it is unreliable stem from the fact the protocol does not provide any functionality for error recovering for datagrams that are either duplicated, lost or arrive to the remote host in another order than they are send. If no such errors occur in the physical layer, the IP protocol guarantees that the transmission is terminated successfully.
The protocol stack is an implementation of a computer networking protocol suite. The terms are often used interchangeably. Strictly speaking, the suite is the definition of the protocols, and the stack is the software implementation of them. Individual protocols within a suite are often designed with a single purpose in mind. This modularization makes design and evaluation easier. Because each protocol module usually communicates with two others, they are commonly imagined as layers in a stack of protocols. The lowest protocol always deals with “low-level”, physical interaction of the hardware. Every higher layer adds more features. User applications usually deal only with the topmost layers (see also OSI model). In practical implementation, protocol stacks are often divided into three major sections: media, transport, and applications. A particular operating system or platform will often have two well-defined software interfaces: one between the media and transport layers, and one between the transport layers and applications. The media-to-transport interface defines how transport protocol software makes use of particular media and hardware types (“card drivers”). For example, this interface level would define how TCP/IP transport software would talk to Ethernet hardware. Examples of these interfaces include ODI and NDIS in the Microsoft Windows and DOS environment. The application-to-transport interface defines how application programs make use of the transport layers. For example, this interface level would define how a web browser program would talk to TCP/IP transport software. Examples of these interfaces include Berkeley sockets and System V STREAMS in the Unix world, and Winsock in the Microsoft world.
One could combine the two protocols to form a powerful third, mastering both cable and wireless transmission, but a different super-protocol would be needed for each possible combination of protocols. It is easier to leave the base protocols alone, and design a protocol that can work on top of any of them (the Internet Protocol is an example.) This will make two stacks of two protocols each. The inter-network protocol will communicate with each of the base protocol in their simpler language; the base protocols will not talk directly to each other.
The Protocol Stack
The Internet consists of many millions of computers on tens of thousands of networks. It is arguably the most complex system ever assembled by mankind. How can such a complex system function reliably, particularly when it grows several times larger every year? The answer is that the Internet is assembled from components that have been built by many manufacturers to a common set of standards. The most fundamental of these standards, the ones we consider in this book, relate to a basic set of functions that has been defined collectively by the networking industry. At the core of these functions isa set of rules for exchanging information. These rules are known as protocols.
Five-layer protocol stack
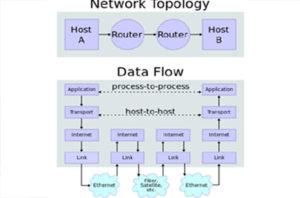
Application Layer: Responsible for whatever the user wants the computer to do, such as interacting with a remote computer, transferring files, or displaying graphics obtained over the World Wide Web (which we refer to in this book simply as the Web). This interaction is achieved by sending messages.
Transport Layer: Responsible for packaging data for host-to-host delivery. For long streams of data, this requires dividing the information into segments. This layer also provides a means to identify how messages are to be used in the receiving host in that a set of messages is associated with a particular application. In many cases, this layer also keeps track of information flow between sender and receiver (which can be anywhere in the network) so that no information is lost or presented to the receiving application layer out of order.
Network Layer: Responsible for putting the segments into “electronic envelopes” called packets and providing the organization necessary to get the packets from sender to receiver. This process involves providing a consistent means of addressing (locating) the sender and receiver as well as a workable means of routing the packets through the communications links, routers, and gateways of the Internet. With good routing, the packets will flow efficiently and will be moved to another path quickly if problems arise.
Data Link Control (DLC) Layer: Responsible for controlling operation of a single data communication link to move information efficiently from end to end, even though the link may be experiencing transmission errors. An important function of this layer is Medium Access Control (MAC), which allows multiple computers to share a single information channel, as shown in Figure 1.3. Other DLC functions include putting delimiters around the packet to make a frame, detecting (and possibly correcting) transmission errors, and controlling the rate at which the sender transmits so the receiver is not overwhelmed with data.
Physical Layer: Responsible for passing information between two physical locations. In its simplest form, the physical layer is a wire. In most cases, it is considerably more complex, being derived from a larger telecommunications system that supports a variety of uses (mostly commercial telephone service)